摘 要
随着计算机网络的日益普及以及因特网的迅速发展,网络已经广泛应用到了个人,团体和政府部门之间的通信。网络安全和隐私通信日渐受到人们的关注和重视,许多因特网应用都需要匿名支持,匿名通信的研究成为当前的一个研究热点。为了满足各种隐私需求,我们有必要研究匿名通信的相关技术。
P2P网络中主要采取重路由技术进行匿名通信,而采取重路由技术的匿名机制有Mix和洋葱路由。Mix机制为实现匿名通信技术提供了可行的解决方案,但攻击者仍可以在一定程度上通过流量分析来获取通信关系。为了进一步提高Mix机制对抗信息量分析攻击的能力,提出了分组填充的思想,并基于分组填充Mix策略给出了一种新型匿名通信机制。与传统Mix机制相比,新的基于分组填充的Mix机制,能在有效抵御信息量分析攻击的同时,进一步降低网络的额外带宽开销。
最后,利用NS2对基于分组填充Mix机制和基于P2P网络的Mix网络通信进行了模拟。
关键词:P2P;NS2;Mix;匿名通信;分组填充
Research of the anonymous communications algorithm in P2P network
Abstract
With the rapid progress of information technologies, computer networks have been widely used in communications among individuals, parties and governments. Concerns on security of network and privacy of communication have been grown. Anonymity needed by many applications on Internet, A research focus which become present of research of anonymous communication. We study the problems of partially connected network traffic camouflage, rerouting path selection in anonymity systems and scalar anonymity.
The rerouting path selection is a most popular technology for P2P anonymous communication. It is usually implemented in the Mix mechanism and Onion Routing Protocol. The Mix mechanism has provided a feasible solution for the realization of anonymous communication, but to a certain degree, the attackers can still obtain the correspondence relations through traffic analysis. In order to further improve the ability of Mix mechanism to resist the traffic analysis of message volume, a kind of scheme named group padding is proposed, and based on which, a novel anonymous correspondence mechanism is designed additionally. Compared with the traditional Mix mechanism, the newly proposed Mix mechanism based on group padding scheme can resist traffic analysis of message volume effectively, and needs lower extra bandwidth simultaneously.
Finally, utilize NS2 platform to simulate and analysis about a grouped padding Mix mechanism and the Mix network communication based on P2P.
Key words: P2P;NS2;Mix; anonymous communication;group padding
本论文对P2P中的匿名通信机制进行了探究,了解了重路由技术在P2P匿名通信中的应用。对Mix机制和洋葱路由协议等主要匿名通信机制进行了比较深入的研究。分析了Mix机制和洋葱路由协议的优缺点。
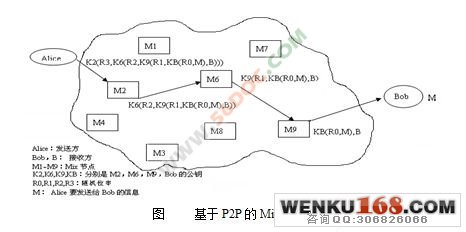
为了抵抗信息量统计攻击,传统Mix机制把所有的数据包填充到一样大,这样势必加重了网络负担,因而提出了一种基于分组填充的Mix机制。基于分组填充的Mix机制能给有效抵抗信息量统计攻击的同时,能使带宽尽可能小。同时对基于P2P的Mix网络进行了模拟,基于P2P的Mix网络没有了洋葱路由技术中首尾两个Mix节点的薄弱环节。
本次毕业设计的另一个重点是使用network simulator version2.29(ns2)对本论文中的匿名通信进行了模拟,ns2是一个强大的网络模拟软件,掌握它的原理和使用方法对以后进行网络方面的学习和研究有很大的帮助,但是学习ns2本身一件工作量比较大的学习过程,经过了近两个月的学习与研究,已对ns2的整个运行原理有了一定的了解,能够添加新的代理协议和包头结构,初步掌握了ns2的基本使用方法。
目 录 18000字
目 录 III
1 绪 论 1
1.1 课题研究背景与意义 1
1.1 国内外研究现状 2
1.1.1P2P系统中的匿名性 3
1.1.2基于P2P的匿名通信机制 4
1.2 论文结构和研究内容 6
1.3 本章小结 6
2 P2P中的一种基于分组填充MIX策略的匿名通信机制 7
2.1 引 言 7
2.2 信息量分析攻击 8
2.3 基于分组填充MIX策略的匿名通信机制 8
2.4 本章小结 9
3 NS2平台简介 10
3.1 NS的简介 10
3.2 NS原理 11
3.2.1丰富的构件库 12
3.2.2离散时间模拟器 11
3.2.3分裂对象模型 12
3.2.4开放的源代码 13
3.3 NS的一般过程 13
3.4 本章小结 14
4 模拟与分析 15
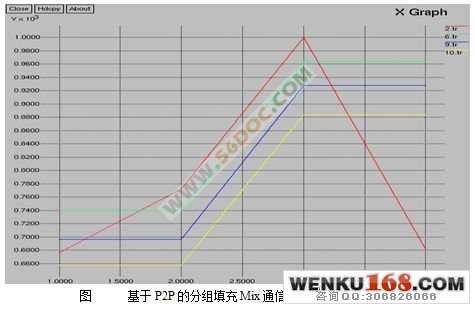
4.1 基于分组填充MIX节点模拟 15
4.1.1MIX基本模型 15
4.1.2模拟过程及结果 15
4.1.3模拟总结 22
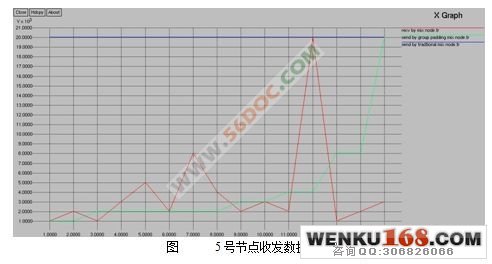
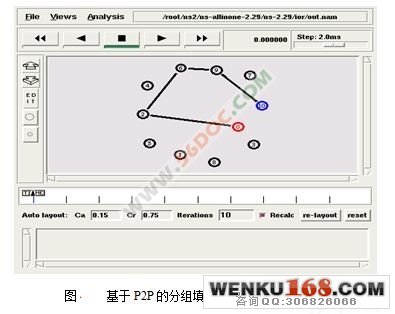
4.2 基于P2P的MIX网络通信模拟 22
4.2.1基于P2P的MIX网络模型 22
4.2.2模拟过程及结果 23
4.2.3模拟总结 27
4.3 本章小结 27
结 论 28
致 谢 29
参考文献 30
附录A:MIX_SIMULATION_RESULT 32
附录B:部分模拟代码 36
附录C:模拟程序环境搭建说明 44
参考文献
[1] 徐红云.匿名通信系统中重路由及分级匿名技术研究[D] .长沙:中南大学信息科学与工程学院,2005.
[2] 吴振强.匿名通信技术的研究现状与展望[J].山西师范大学学报(自然科学版) ,2002,30(4) :107-111.
[3] 李超.基于P2P的匿名技术研究[D] .北京:北京图形研究所,2005.
[4] 李旭华.P2P网络中基于代理合作的匿名传输机制[J] .计算机应用,2006,26(1) :20-35.
[5] 王伟平.匿名通信系统性能及可扩展性研究[D] .长沙:中南大学,2004.
[6] 申鹏琳.洋葱路由协议的研究与NS2仿真[D] .长沙:湖南大学,2006.
[7] Andrew S.Tanenbaum 著.计算机网络[M] . 北京:清华大学出版社,2005.
[8] 匿名相关论文.
[9] Jakabsson M.Yung M.Revocable and versatile electronic money[A].Third ACM Conference on Computer and Communication Security [C] .India:1996.
[10] Camenish J.Maurer U.Stadler M.Digital payment systems with passive anonymity revoking trustees[J] .Journal of Computer Security,1997,5 (1) :78-100.
[11] Chaum D.Untraceable electronic mail,return addresses,and digital pseudonyms[J] .Communications of the ACM,1981,24(2) :84-90.
[12] D.Goldschlag,M.Reed and P.Syverson.Onion Routing for Anonymous and Private Internet Connections[J] .Communications of the ACM,1999,42(2) :39-41.
[13] Dogan Kesdogan,Jan Egner and Roland Büschkes.Stop-and-Go MIXes:Providing Probabilistic Anonymity in an Open System[A] .In the Proceedings of Information Hiding Workshop (IH 1998) [C],1998.
[14] Rob Sherwood,Bobby Bhattacharjee,and Aravind Srinivasan.P5 :A Protocol for Scalable Anonymous Communication[A] .In the Proceedings of the 2002 IEEE Symposium on Security and Privacy[C] ,May 2002.
[15] Michael J.Freedman and Robert Morris.Tarzan:A Peer-to-Peer Anonymizing Network Layer[A] .In the Proceedings of the 9th ACM Conference on Computer and Communications Security (CCS 2002)[C] ,Washington.DC,November 2002.
[16] Ulf Möller,Lance Cottrell,Peter Palfrader and Len Sassaman.Mixmaster Protocol — Version 2.July 2003.
[17] George Danezis,Roger Dingledine,Nick Mathewson.Mixminion:Design of a Type III Anonymous Remailer Protocol[A] .In the Proceedings of the 2003 IEEE Symposium on Security and Privacy[C] ,May 2003.
[18] Marc Rennhard and Bernhard Plattner.Introducing MorphMix:Peer-to-Peer based Anonymous Internet Usage with Collusion Detection[A] .In the Proceedings of the Workshop on Privacy in the Electronic Society (WPES 2002)[C] ,Washington.DC,USA ,November 2002. |




