MD5算法的研究与实现-数据存储加密
来源:wenku163.com 资料编号:WK1632089 资料等级:★★★★★ %E8%B5%84%E6%96%99%E7%BC%96%E5%8F%B7%EF%BC%9AWK1632089
资料介绍
摘 要
随着网络技术的广泛应用,网络信息安全越来越引起人们的重视。针对数据在存储的时候存在大量的安全问题,目前通常将需要存储的数据进行加密然后再存储,应用MD5算法是一个不错的选择。MD5算法的全称是Message-Digest algorithm 5,是一种用于产生数字签名的单项散列算法。它的作用是让大容量信息在用数字签名软件签署私人密钥前被“压缩”成一种保密的格式,即将一个任意长度的“字节串”通过一个不可逆的字符串变换算法变换成一个128bit的串。
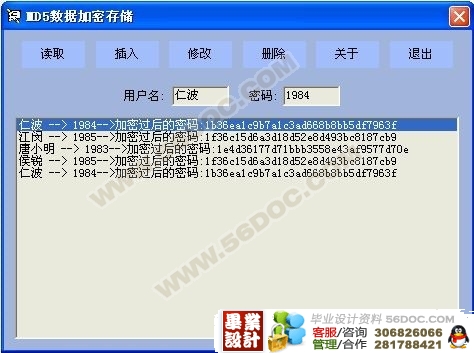
该毕业设计是运用microsoft visual c++ 6.0软件而开发的,主要是通过算法实现数据的加密存储。文章分成五部分。第一,二部分描述了MD5的目前现状和相关理论知识,也让我们了解MD5的定义。重点是MD5的流程实现和封装DLL。在MD5算法的DLL封装这章,主要是描述我们为什么要选用封装DLL的原因,以及封装的好处。设计流程这一部分里包含读取,修改,插入,删除这几个功能的实现情况,并用流程图的方式来分别描述了这四大功能模块的实现过程。最后一部分显示了系统测试的内容和系统主要功能运行界面图。
关键词:信息安全;MD5;加密;封装
The Research and Implementation for MD5 Algorithm
-------- Data Storage and Encryption
Abstract
With the wide application of the network technology, the information of the network safety causes people’s attention more and more. A large number of security questions appear while storing data, the data that usually store needing at present are encrypted then stored, it is a good choice to use MD5 algorithm. The full name of MD5 algorithm is Message-Digest algorithm 5, is that a kind of individual event used for producing figures and signed breaks up and arranges algorithms. Its function is to let large capacity information " compress " and become a kind of secret form before signing the private key with the digital signature software, vary " byte bunch " of a wanton length into a great integer of one 128bit through an irreversible one bunch of algorithms of varying of character .
Used Microsoft Visual C++ 6.0 software and developed in this graduation project, is mainly to realize through the algorithm that the encryption of the data is stored. The article is divided into five parts. The first and second parts are describing the current situation and relevant theory knowledge at present of MD5, let us understand the definition of MD5. The focal point is the procedure of MD5 is realized and encapsulation to Dynamic Link Library. In this chapter of encapsulation MD5 class library to Dynamic Link Library, mainly describe why we will select encapsulation Dynamic Link Library for use , and the advantage of encapsulation . Design this of procedure and include reading in the part , revise , insert, delete the realization situations of these functions, and has described the realization course of this four major functions module respectively in way of the flow chart . The last part has shown that the content of system testing and main function of system operate the interface picture .
Key words: information security; MD5; encrypt; Packaging
 |

